Staying Fit
Criminals hunger for your Social Security number, date and place of birth, mother's maiden name, and other identifiers. They siphon information from data breaches, the dark web and public sources such as social media sites and employee directories. Using subterfuge, they have no qualms about trying to pry it directly out of you. This personal data fuels a long list of financial crimes. Here are a dozen of the most common tactics used by scammers to fool victims and perpetuate fraud.
1. Spoofing
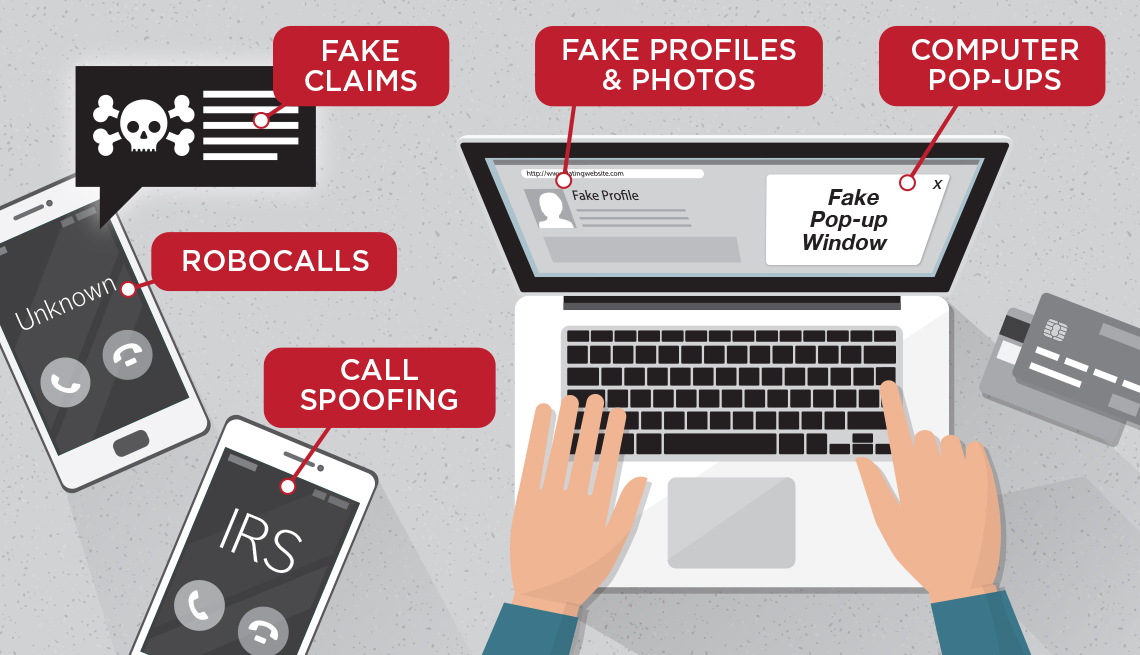
Does caller ID show the same area code and prefix as yours? That incoming call could be from anywhere — even a foreign country. Spoofing is falsifying data on caller ID to disguise who's on the line. In a bid for authenticity, the spoofed number could belong to a legitimate government agency or a business known to you.


AARP Membership— $12 for your first year when you sign up for Automatic Renewal
Get instant access to members-only products and hundreds of discounts, a free second membership, and a subscription to AARP the Magazine.
2. Phishing
So-called “phishing” emails, calls, texts and letters try to trick you into sending cash or disclosing personal information. Or, the correspondence aims to allow a bad actor to infiltrate your computer device and steal sensitive information. Microsoft, for example, has warned that cybercrooks send phishing emails from rnicrosoft.com—note the “r” and “n” were combined to appear at a glance as an “m.” The word phishing — which dates to 1996 — combines “fishing” and “phreaking,” the latter a term for using an electronic device to avoid paying for phone calls, says Merriam-Webster. Phreaking likely was born from the marriage of the words “phone” and “freak."
3. Fake profiles
Anybody can disguise his or her identity on social media, dating platforms or other sites. In 2019, the Pentagon warned about an increasing number of impersonator accounts on Twitter that hijacked the identity of Marine Gen. Joseph Dunford, then chairman of the Joint Chiefs of Staff. That prompted the Air Force chief of staff to chime in: “The same goes for me — I won't ask for money, your email account or other personal information. Please continue to report impostor pages."
4. Fake photos
Images can be copied or stolen from the internet — or altered — to lend credence to a bogus profile or website.